PROTOCOLS
Introduction
The internet protocols are modelled in four layers
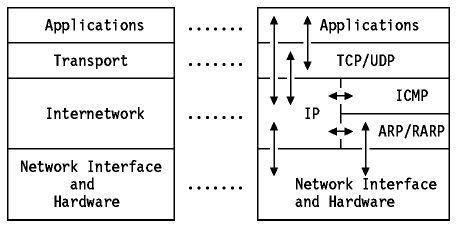
Application Layer
The protocols implemented at this layer are TELNET (a protocol for
remote terminal connections), FTP (File Transfer Protocol)
and SMTP (Simple Mail Transfer Protocol)
Transport Layer
The protocols implemented at this layer are TCP (connection-oriented)
and UDP (connectionless).
Internetwork
Internet Protocol (IP) is the most important protocol in this layer.
Other protocols are ICMP, ARP , RARP
Network Interface
Protocols at this layer are IEEE 802.2, X.25 (which is reliable in itself), ATM,FDDI,Packet Radio Networks (such as the AlohaNet) and even SNA. The
possible physical networks and interfaces.
Protocols
ARP
On a single physical network, individual hosts are known on the network by
their physical hardware address. Higher level protocols hosts in the form
of a symbolic address (IP address in this case). When such a protocol wants
to send a datagram address w.x.y.z, the device driver does not understand
this address.Therefore, a module (ARP) is provided that will translate the
IP address to the physical address of the destination host. It uses a lookup
table (sometimes referred to as the ARP cache) to perform this translation.
When the address is not found in the ARP cache, a broadcast is sent out on
the network, with a special format called
the ARP request. If one of the machines on the network recognizes its own
IP address in the request, it will send an ARP reply back to the
requesting host. The reply will contain the physical hardware address of
the host and source route information. Both this address
and the source route information are stored in the ARP cache of the requesting
host. All subsequent datagrams to this destination IP
address can now be translated to a physical address, which is used by the
device driver to send out the datagram on the network.
RARP
The RARP protocol is a network-specific standard protocol. Some network
hosts, such as diskless workstations, do not know their own IP address
when they are booted. To determine their own IP address, they use a mechanism
similar to ARP (Address Resolution Protocol), but now the hardware address of the host is the known parameter,and the IP address the queried parameter.
It differs more fundamentally from ARP in the fact that a "RARP server" must exist on the network which maintains a database of mappings from hardware address
to protocol address.RARP requires one or more server hosts on the network
to maintain a database of mappings between hardware addresses and protocol
addresses so that they will be able to reply to requests from client hosts.
Internet Protocol
The Internet Protocol (IP) is a network-layer (Layer 3) protocol that contains
addressing information and some control information that enables packets to be routed. IP is documented in RFC 791 and is the primary network-layer
protocol in the Internet protocol suite. Along with the Transmission Control
Protocol (TCP), IP represents the heart of the Internet protocols.
IP has two primary responsibilities: providing connectionless, best-effort
delivery of datagrams through an internetwork; and providing fragmentation
and reassembly of datagrams to support data links with different maximum
-transmission unit (MTU) sizes.
IP PACKET FORMAT
Version
Indicates the version of IP currently used.
IP Header Length (IHL)
Indicates the datagram header length in 32-bit words.
Type-of-Service
Specifies how an upper-layer protocol would like a current datagram to be
handled, and assigns datagrams various levels ofimportance.
Total Length
Specifies the length, in bytes, of the entire IP packet, including the data
and header.
Identification
Contains an integer that identifies the current datagram. This field is used
to help piece together datagram fragments.
Flags
Consists of a 3-bit field of which the two low-order (least-significant) bits
control fragmentation.The low-order bit specifies whether the packet can be
fragmented. The middle bit specifies whether the packet is the last fragment
in a series of fragmented packets. The third or high-order bit is not used.
Fragment Offset
Indicates the position of the fragment's data relative to the beginning of
the data in the original datagram, which allows the destination IP process to properly reconstruct the original
datagram.
Time-to-Live
Maintains a counter that gradually decrements down to zero, at which point
the datagram is discarded.This keeps packets from looping endlessly.
Protocol
Indicates which upper-layer protocol receives incoming packets after IP processing is complete.
Header Checksum
Helps ensure IP header integrity.
Source Address
Specifies the sending node.
Destination Address
Specifies the receiving node.
Options
Allows IP to support various options, such as security.
Data
IP Addressing
As with any other network-layer protocol, the IP addressing scheme is integral
to the process of routing IP datagrams through an internetwork. Each IP address has specific components and follows
a basic format. These IP addresses can subdivided and used to create addresses for subnetworks.Each host on a
TCP/IP network is assigned a unique 32-bit logical address that is divided into two main parts: the network
number and the host number. The network number identifies a network and must be assigned by the Internet Network
Information Center (InterNIC) if the network is to be part of the Internet. The 32-bit IP address is grouped eight
bits at a time, separated by dots, and represented in decimal format (known as dotted decimal notation). Each bit
in the octet has a binary weight (128, 64,32,16, 8, 4, 2, 1).The minimum value for an octet is 0, and the maximum
value for an octet is 255. IP addressing supports five different address classes: A, B,C, D, and
E. Only classes A, B, and C are available for commercial use.
UDP
UDP is basically an application interface to IP. It adds no reliability, flow-control or error
recovery to IP. It simply serves as a ``multiplexer/demultiplexer'' for sending and receiving datagrams, using
ports to direct the datagrams. UDPprovides a mechanism for one application to send a datagram
to another. The UDP layer can be regarded as being extremely thin and consequently has low overheads, but
it requires the application to take responsibility for error recovery and so on. Applications sending datagrams to
a host need to identify a target which is more specific than the IP address, since datagrams are normally directed
to certain processes and not to the system as a whole. UDP provides this by using ports. A port is a 16-bit number
which identifies which process on a host is associated with a datagram.Standard applications using UDP include:
- Trivial File Transfer Protocol (TFTP)
- Domain Name System (DNS) name server
- Remote Procedure Call (RPC), used by the Network File System (NFS)
- Network Computing System (NCS)
- Simple Network Management Protocol (SNMP)
TCP
The primary purpose of TCP is to provide reliable logical circuit or connection service between pairs of processes. It does not assume reliability from the
lower-level protocols (such as IP)so TCP must guarantee this itself. TCP can
be characterized by the following facilities it provides for the applications
using it:
Stream Data Transfer
From the application's viewpoint, TCP transfers
a contiguous stream of bytes through the internet. The application does not
have to bother with chopping the data into basic blocks or datagrams.
TCP does this by grouping the bytes in TCP segments, which are
passed to IP for transmission to the destination. Also, TCP
itself decides how to segment the data and it may forward the data at
its own convenience.
Reliability
TCP assigns a sequence number to each byte transmitted,
and expects a positive acknowledgment (ACK) from the receiving TCP.
If the ACK is not received within a timeout interval,
the data is retransmitted. As the data is transmitted in blocks (TCP segments)
only the sequence number of the first data byte in the segment is
sent to the destination host. The receiving TCP uses the sequence
numbers to rearrange the segments when they arrive out of order, and
to eliminate duplicate segments.
Flow Control
The receiving TCP, when sending an ACK back
to the sender, also indicates to the sender the number of bytes it
can receive beyond the last received TCP segment, without causing
overrun and overflow in its internal buffers. This is sent in the ACK in
the form of the highest sequence number it can receive without problems.
This mechanism is also referred to as a window-mechanism.
Multiplexing
Is achieved through the use of ports, just
as with UDP.
Logical Connections
The reliability and flow control mechanisms described above require
that TCP initializes and maintains certain status information
for each ``data stream''. The combination of this status, including sockets,
sequence numbers and window sizes, is called a logical
connection. Each connection is uniquely identified by the pair of sockets
used by the sending and receiving processes.
Full Duplex
TCP provides for concurrent data streams in both directions
reference: http://www4.ulpgc.es/tutoriales/tcpip/pru/
